Carter Dack, 2021.
The following report presents a proof of concept for the potential risks associated with unpatched vulnerabilities in computer systems and networks. Vulnerabilities in software and systems can leave organizations and individuals open to exploitation by malicious actors seeking to gain unauthorized access to sensitive information or disrupt operations.
The objective of this proof of concept is to demonstrate how an attacker could potentially gain remote access to a vulnerable system using the Metasploit framework. Metasploit is an open-source penetration testing tool used by security professionals to identify security flaws in computer systems and networks. While Metasploit is often used for ethical purposes such as identifying and fixing vulnerabilities, it can also be used by malicious actors to gain unauthorized access to systems.
This proof of concept highlights the importance of maintaining up-to-date security practices and implementing regular vulnerability assessments and patches. Organizations and individuals that fail to keep their systems updated are at risk of being compromised by attackers seeking to exploit known vulnerabilities.
It is important to note that this proof of concept is intended for educational purposes only and should not be used to conduct unauthorized or malicious activities. The purpose of this exercise is to raise awareness of the potential risks associated with unpatched vulnerabilities and to encourage proactive security measures to prevent attacks.
Machine IP: 192.168.0.20
Hostname: MSEDGEWIN10
Vulnerability Exploited: exploit/windows/http/icecast_header
Vulnerability Explanation:
The icecast exploit is a type of buffer overflow attack that targets the header parsing functionality of the icecast streaming server versions 2.0.1 and earlier. The vulnerability exists because the server fails to properly validate user input in the header parsing function, leading to a buffer overflow condition.
The exploit works by sending 32 HTTP headers to the server, causing a write one past the end of a pointer array. This can cause unexpected behavior in the program, such as overwriting important memory locations or even executing arbitrary code. On Windows systems, the exploit can overwrite the saved instruction pointer, allowing the attacker to take control of the execution flow and execute arbitrary code.
Severity:
The vulnerability in question represents a severe threat to the security of the affected system. Depending on the level of external exposure, this vulnerability has the potential to leave the machine in a fundamentally insecure state. The ability to execute arbitrary code with the privileges of the targeted application or service poses a significant risk to the confidentiality, integrity, and availability of the system.
Given the potential consequences of exploitation, it is imperative that organizations take immediate action to mitigate the risks associated with this vulnerability. The ability to execute arbitrary code allows an attacker to gain complete control over the system and escalate privileges. This presents an endless array of possibilities for an attacker to carry out malicious activities, including the theft of sensitive data, the installation of malware, or the disruption of normal operations.
Proof of Concept:
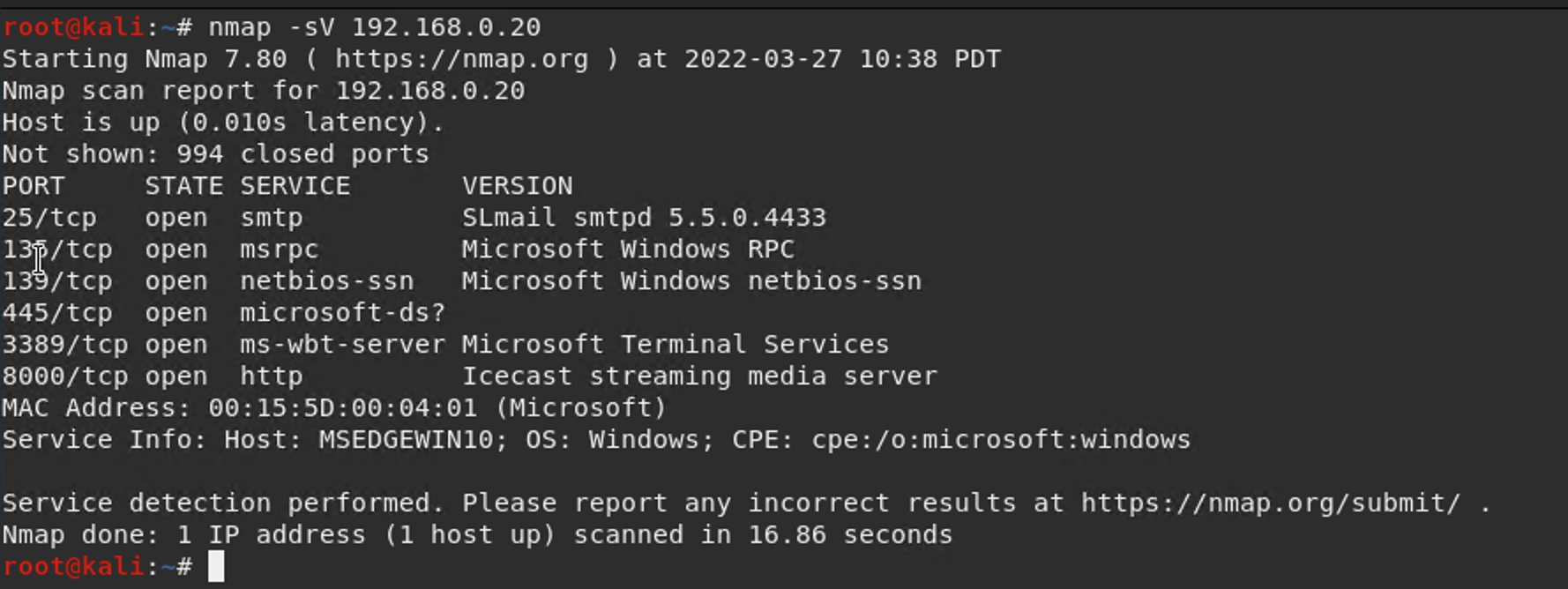
Conducting a thorough service and version scan of a target machine is a critical step in identifying potential vulnerabilities and determining the overall security posture of the system. The use of a tool such as Nmap can aid in this process by providing valuable information about the services that are currently running on the target machine.
FIGURE 1.1 - Target Scanning
Upon completion of the initial reconnaissance phase, the next step in a targeted attack is to identify potential vulnerabilities in the target system. In the case of the Icecast service, a search for known exploits can be a useful starting point.
Figure 1.2 - Icecast Exploits
With the identification of a potential exploit targeting the Icecast service, the next step in a targeted attack is to leverage the exploit to gain unauthorized access to the target system. The desired exploit is queued up within the metasploit console.
Figure 1.3 - Load Exploit
Figure 1.4 - Defining Target
Figure 1.5 - Executing Exploit
Post Exploitation
Data exfiltration refers to the unauthorized removal of data from a system or network. This can occur when an attacker gains access to sensitive information, such as personal or financial data, intellectual property, or confidential business information, and extracts it from the target system without authorization.
Data exfiltration can take many forms, including the use of file transfer protocols, email, or cloud-based storage services to transmit the stolen data to an external location. Attackers may also use covert channels, such as steganography, to hide the stolen data within seemingly innocuous files or images.
The consequences of data exfiltration can be severe, as it can result in the theft of sensitive or confidential information, damage to a company's reputation, loss of intellectual property, and legal or regulatory consequences.
Once unauthorized access has been gained to the target system using the Metasploit Framework, the attacker can leverage its native shell to exfiltrate data from the victim to the attacker's machine. This technique involves copying sensitive data from the target system to the attacker's machine, often through covert channels such as encrypted network connections or hidden file transfer protocols.
Figure 2.1 - Data Exfil
In addition to its powerful shell functionality, the Metasploit Framework includes the Meterpreter post-exploitation module. Meterpreter provides an interactive shell that enables the attacker to execute arbitrary commands on the target system, access its file system, and manage running processes.
One particularly useful feature of Meterpreter is its local exploit suggester, which analyzes the target system and suggests additional exploits that could be used to further exploit the system. This capability is particularly valuable in cases where the initial exploit was successful, but additional access is needed to accomplish the attacker's objectives.
Figure 2.2 - Exploit Suggester
In light of the severe vulnerability discovered in the Icecast service, it is recommended that the service is immediately updated to the latest version. Updating the service will ensure that the current functional exploit can no longer be used to compromise the system. Once the Icecast service has been updated, it is recommended to filter it with a firewall, only allowing access to users who require the service. This will help to mitigate the risk of unauthorized access and further exploitation.
In addition to updating and filtering the Icecast service, it is recommended that all other services running on the target system are also updated and filtered as necessary. This will help to ensure that all known vulnerabilities are patched and that access to services is restricted to authorized users only.
Furthermore, the Meterpreter module's local exploit suggester identified two additional potential exploits, ikeext_service and ms16_075_reflection, that should be taken into consideration during the vulnerability remediation process. Appropriate measures, such as filtering or disabling these services where possible, should be taken to prevent exploitation of these vulnerabilities.