Back
Understanding and Combating Spam, Junk, and Phishing Emails: A Comprehensive Guide
In the digital era, email communication has become indispensable, but it also serves as a fertile ground for cyber threats like spam, junk, and phishing emails. This comprehensive analysis delves into the intricacies of these malicious emails, providing insights into their structure, behavior, and the methodologies employed by cybercriminals.
HTML Structure of Malicious Emails
A common characteristic of these emails is their HTML composition. They frequently contain embedded URLs, which, upon being clicked, activate and lead the user to a Google Cloud storage resource or similar platform. This technique is particularly effective as it can bypass basic email filters that are designed to flag suspicious links. Screenshots of rendered HTML for legitimate malicious emails can be seen below in Figure I.
Figure I - Rendered HTML of Real Emails

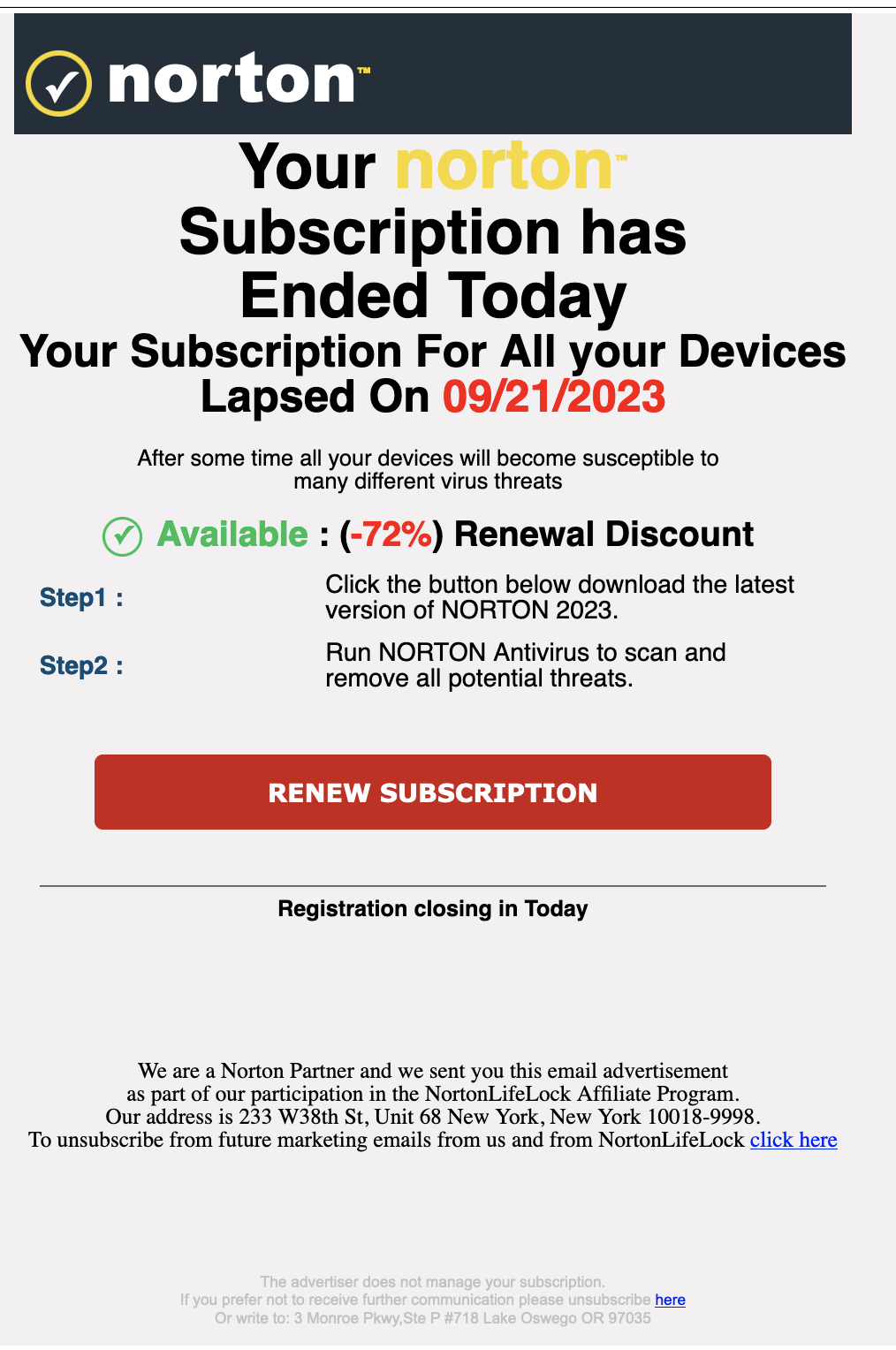
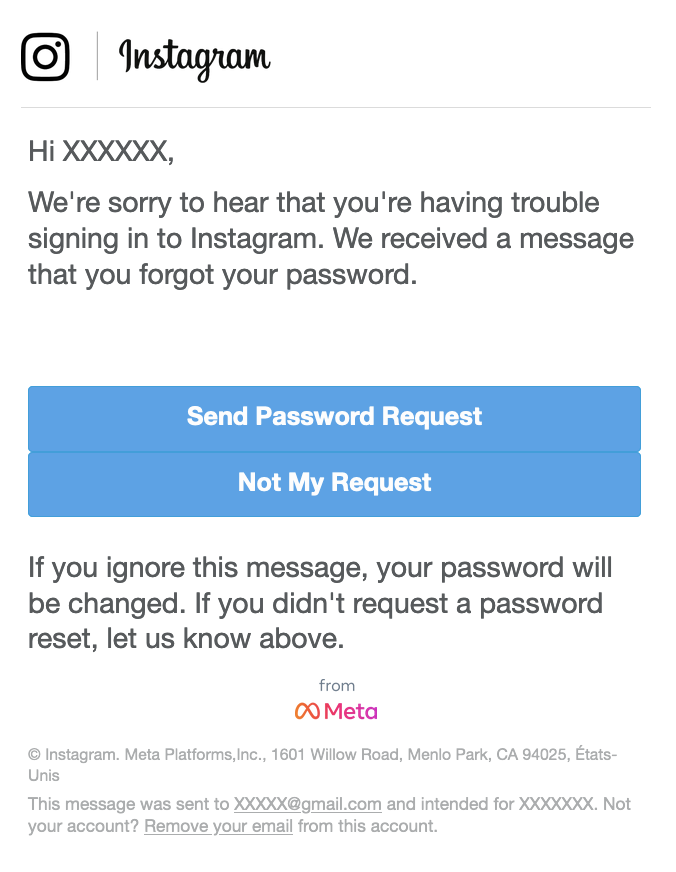
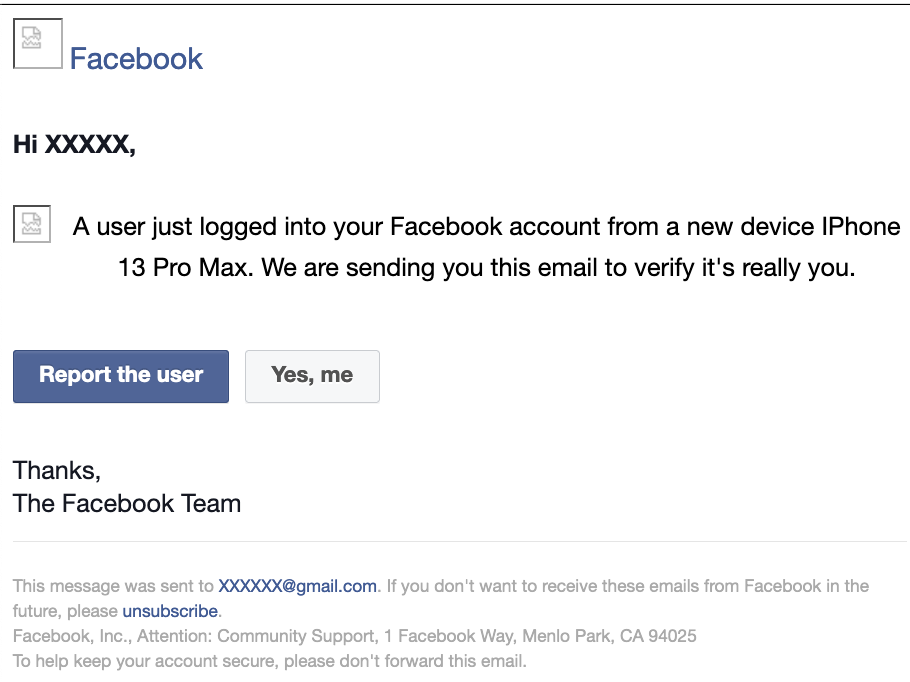
Note: To understand current Tactics, Techniques, and Procedures (TTPs) real email samples were analyzed. Thanks to those who contributed these samples. Caution is advised against attempting to interact with or analyze malicious emails, as there is a risk of falling victim to these sophisticated attacks.
Initial Observations
- Most emails are written in the HyperText Markup Language (HTML)
- Most emails contain one URL that will be opened if the user clicks anywhere within the email. Many times this URL will be a storage.googleapis.com or other cloud resource.
- Emails will often contain misspellings, strange or inconsistent formatting, urgent language, and they may often mimic a commonly used service such as Netflix or Instagram.
JavaScript and URL Manipulation
JavaScript often plays a crucial role in these emails. It is often used to redirect users to different webpages based on certain triggers or actions and this redirection can lead unsuspecting users to malicious websites, where they are vulnerable to further exploitation.
Upon accessing a linked resource, a user is provided the following JavaScript, which is automatically run by the user’s browser when rendering the web page.
Figure II - Malicious Javascript
<script>
document.location.href = 'http://new-url.com/anchor' + window.location.href.split('#')[1];
</script> |
The above JavaScript code takes the fragment identifier (the part of a URL after the '#' symbol) from the original URL and appends it to a newly crafted URL. In this case, the fragment identifier in the original URL is a base64 encoded string. For demonstration purposes, we can use the following URLs and values:
Key:
= Base Google Cloud storage URL
= Unique Google Cloud directory owned by the Threat Actor (the name may be a random string of characters)
= HTML file containing the malicious JavaScript code as seen in Figure II
= Fragment Identifier
= New URL contained in JavaScript code
Original URL Contained in Email:
https://storage.googleapis.com/uniquedirectory/randomstring.html#VGhhbmsgeW91IGZvciByZWFkaW5nISEgZG9uJ3QgdHJ5IHRoaXMgYXQgaG9tZSBraWRzIQ==
JavaScript Converted URL:
http://new-url.com/anchor#VGhhbmsgeW91IGZvciByZWFkaW5nISEgZG9uJ3QgdHJ5IHRoaXMgYXQgaG9tZSBraWRzIQ==
After constructing the new URL, the JavaScript code will instruct the browser to navigate to this new site. Upon requesting the new URL resource, a user is served with yet more JavaScript as seen in Figure III.
Figure III - Even More Malicious JavaScript
<script type="text/javascript">
function getHash() {
if (window.location.hash) {
var hash = window.location.hash.substring(1);
if (hash.length > 5) {
return hash;
} else {
return false;
}
} else {
return false;
}
}
var hashCode = getHash();
var dom = "http://" + window.location.hostname;
if (hashCode) {
var url = dom + "/" + hashCode;
} else {
var url = dom + "/404.html";
}
window.location.replace(url);
</script> |
This Javascript simply checks whether the “hash” value (or the URL fragment) is present and greater than 5 characters. If it is not, the user is directed to a 404 page, and if it is, the URL is re-organized to look like the below, the only change being the removal of the “anchor” and fragment component.
http://new-url.com/VGhhbmsgeW91IGZvciByZWFkaW5nISEgZG9uJ3QgdHJ5IHRoaXMgYXQgaG9tZSBraWRzIQ==
Up to this point, the user has not seen anything particularly interesting within their browser other than various loading operations and new URLs populating in the URL bar. Oftentimes, this URL manipulation via JavaScript can continue many times over before reaching a final renderable webpage, but eventually a user will wind up on some sort of webpage. In this case, the user is presented with an “Unsubscribe” action as seen in Figure IV.
Figure IV - Unsubscribe

Upon entering an email address, and clicking the ‘aaa’ button, a GET request will be made to the following URL:
http://new-url.com/[email protected]
Unfortunately, the php script seems to be a backend script that is not directly viewable to a user. Instead, the server looks to be configured to execute the PHP script and generate HTML or other output, which is then sent to the user's browser. It may be possible in this case, that this spam email is used to collect valid email addresses of users who have a high likelihood of “falling for” a spam email, to later be sent more malicious content, however without further investigation, it may be difficult to know for sure.
Email Header Analysis
Email headers can reveal a wealth of information about the origin of an email. In the case of phishing emails, inconsistencies in email sender and return domain infrastructure are common red flags. Additionally, the absence or misconfiguration of SPF records in the email header can indicate a spoofed email.
Figure V - Email Headers of Malicious Email
Delivered-To: [email protected]
[...]
Return-Path: <[email protected]>
Received: from facebook.com (static.171.153.235.167.clients.your-server.de. [167.235.153.171])
[...]
Received-SPF: pass (google.com: domain of [email protected] designates 167.235.153.171 as permitted sender) client-ip=167.235.153.171;
Authentication-Results: mx.google.com;
dkim=temperror (no key for signature) [email protected] header.s=smtp header.b=UpPF3q4S;
spf=pass (google.com: domain of [email protected] designates 167.235.153.171 as permitted sender) [email protected]
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=smtp; d=har-freight.us;
[...]
From: Harbor Freight Winner <[email protected]>
subject: XXXXXX 170 Piece Stanley Tool Set - Your order has shipped! CUSTOMER #XXXX
X-Google-Sender-Delegation: Harbor-Freight
To: [email protected]
Message-ID: <[email protected]> |
Observations
- Origins and Claims: The email was sent from the domain "mail.761350.com" but claims to be from "[email protected]" and directs responses to "[email protected]".
- Domain Control: The sender controlled two domains: "mail.761350.com" for sending the email and "z6d8f0d7eg.streamagram.hk.com" for handling replies. The latter domain also authorizes the former to send emails on its behalf.
- Geographic and Domain Mismatch: The sending domain "mail.761350.com" was registered in China but used a German IP address. This domain has since expired, indicating it was likely used temporarily, a common tactic in phishing to avoid detection.
- Complex SPF Record: The SPF record of "z6d8f0d7eg.streamagram.hk.com" includes several other domains, creating a complex network that makes it harder to identify as a threat. Despite a strict SPF policy, the inclusion of many domains suggests a deliberate attempt to confuse.
- Inconsistencies in Sender Information: There's a mismatch between the email's display sender address ("[email protected]") and the return path ("z6d8f0d7eg.streamagram.hk.com"). This inconsistency is often a sign of email spoofing.
- Misleading Brand Association: The email header includes "X-Google-Sender-Delegation: Harbor-Freight," implying an association with Harbor Freight. However, this is likely false since the other details don’t match what you’d expect from a genuine Harbor Freight email.
- DKIM Signature Error: A 'temperror' in the DKIM signature suggests a problem with the email’s digital signature. This raises doubts about the email's authenticity, as it may not have been properly authenticated.
Preventative Measures
Organizations should implement sophisticated email filtering solutions that employ a multi-layered approach to security. Key components include:
- Machine Learning Algorithms: Utilize machine learning to analyze patterns and anomalies in email content, which can predict and identify new phishing tactics.
- Domain Authentication Protocols: Implement protocols like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) to authenticate email senders and ensure the integrity of the messages.
- URL Analysis and Reputation Scoring: Deploy systems that scrutinize URLs within emails for known malicious domains and perform real-time reputation scoring based on various threat intelligence sources.
- Attachment Sandboxing: Use sandboxing techniques to analyze email attachments in a controlled environment, detecting malicious payloads before they reach the user.
- Anomaly Detection Systems: Employ anomaly detection to flag unusual sender behavior, such as sudden changes in email volume or atypical sending locations.
Legal and Ethical Considerations
The legal landscape surrounding phishing and spam emails is shaped by several critical laws and regulations, designed to deter these malicious activities and protect victims. Key legal frameworks include:
- The CAN-SPAM Act (USA): This act sets forth clear guidelines for commercial email communication. It mandates transparency in messaging, prohibits deceptive subject lines and false headers, and requires that recipients be given an easy way to opt-out of future emails. Violators can face significant penalties, emphasizing the act's role in curbing unwanted and deceptive email practices.
- General Data Protection Regulation (GDPR) (EU): GDPR represents a significant shift in data privacy regulation, with a global impact on data protection practices. It demands stringent data handling and consent protocols, particularly relevant in the context of phishing attacks that often target personal data. Organizations found in violation of GDPR, especially in cases involving phishing breaches, can face severe financial penalties, making compliance a top priority.
- Computer Fraud and Abuse Act (CFAA) (USA): This act addresses illegal activities associated with computer hacking. It includes provisions against unauthorized access to computers, which covers a range of actions often seen in phishing attacks, such as the illegal access and acquisition of personal and financial information. The CFAA serves as a critical tool in prosecuting cybercrimes and reflects the seriousness with which such offenses are treated.
- Electronic Communications Privacy Act (ECPA) (USA): ECPA protects against unauthorized interception of electronic communications. It is particularly relevant in the context of email security, as it addresses issues related to unauthorized access and disclosure of electronic communications.
In addition to legal requirements, ethical considerations play a crucial role in handling the aftermath of phishing attacks:
- Data Integrity and Confidentiality: Organizations must ensure the integrity and confidentiality of personal data. This involves employing robust security measures to protect data and prevent unauthorized access, especially in the wake of a phishing attack.
- Transparent Communication: In the event of a data breach, transparent communication with stakeholders, including customers and employees, is essential. This transparency helps maintain trust and demonstrates a commitment to ethical practices.
- Cooperation with Law Enforcement: Ethical handling also involves cooperating with law enforcement and regulatory authorities in the investigation and response to phishing attacks. This cooperation is vital in preventing further attacks and holding perpetrators accountable.
- Responsible Disclosure: If a phishing attack leads to a data breach, responsible disclosure to affected parties is not just a legal requirement but an ethical obligation. Timely notification allows individuals to take protective measures against potential misuse of their data.
Conclusion
Based on the comprehensive analysis of spam, junk, and phishing emails, it is clear that these malicious communications present a significant threat in the digital landscape. The intricate HTML structures, the manipulative use of JavaScript and URLs, and the deceptive email headers are all tactics used by cybercriminals to exploit unsuspecting users. These emails often bypass basic security measures, leading to potential breaches of personal and financial information.
Overall, the fight against spam, junk, and phishing emails requires a vigilant and proactive approach, combining technological solutions with legal and ethical practices. As cybercriminals evolve their strategies, so must our defenses, to safeguard our digital communication channels against these pervasive threats.

