Carter Dack, 2023.
Cracked Software: Disassemblers and Threat Landscape
Overview
Cracking software often requires reverse engineering machine-executable binaries which can reveal program functionality in assembly, a low-level language that can be interpreted by humans. Reverse engineering provides insight into program execution and logic and enables manipulation of the program's behavior, such as by circumventing licensing and security features that prevent unauthorized use - a tactic commonly referred to as “Cracking”.
While cracking software may provide cost-free access to individuals without the means or ability to purchase paid software/features, it also has a dark side. Threat actors can leverage these techniques to wield powerful programs such as the CobaltStrike command and control (C2) framework, as well as to insert unknown and potentially malicious program functionality, often proliferating the spread of malware.
This article will seek to provide an in-depth technical demonstration of how reverse engineering can be used to crack paid software as well as provide a look into the current threat landscape and the risks that online cracked software can pose to individuals, organizations, and communities.
Tradecraft
“Cracking” or “Patching” a program is the process of bypassing or removing software copy protection mechanisms to enable the use of a program without a valid license or payment. This can be achieved through various methods, including manipulating the software’s instructions to bypass license checks. When patching software, specific program instructions or values within the software's code may need to be modified to disable its copy protection mechanisms. The cracking process can be challenging and may require extensive research to effectively deactivate a program's copy protection mechanisms depending on its sophistication.
To assist in learning how to crack software, online resources host intentionally vulnerable software. These resources are designed to teach individuals how to identify and bypass different types of copy protection mechanisms. For example, using crackmes.one, a simple program written by LaFarge is downloaded and disassembled, its copy protection mechanisms bypassed, and a newly cracked program is saved.
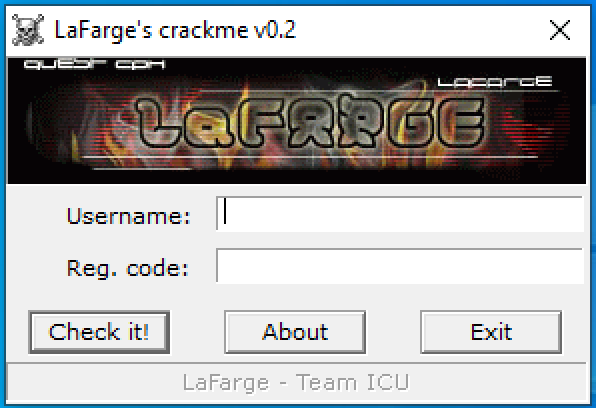
In Figure 1.1, the interface of LaFarge’s sample application requires the user to input a username and registration code.
FIGURE 1.1 - LaFarge’s Crackable Program Interface
The application seems to generate registration codes based on a username and verifies that the entered registration code value matches the generated code. Presumably, users would receive the registration code upon purchasing the application, as illustrated in Figure 1.2.
FIGURE 1.2 - Registration Code Generation
Upon entering an erroneous registration code, the user is confronted with an error message as depicted in Figure 1.3.
FIGURE 1.3 - Invalid Registration Code
Even if the username "test" has not been officially registered or purchased for the software, the copy protection mechanism implemented in the program is somewhat rudimentary, lacking a validation check against a backend server of known valid usernames. Consequently, the registration code is still being generated and can be either bypassed completely or revealed by manipulating the program's logic.
Now that the basic functionality of the program is understood, it is time to get under the hood and disassemble the program’s binary.
A Brief Note on Disassembly
When a program is originally compiled, it is converted from its source code into a binary executable file that contains machine code instructions that can be executed directly by the computer's CPU. Disassembling a binary file is the process of converting the machine code instructions back into assembly language instructions, which are easier for humans to read and understand.
Once machine code instructions have been loaded into a disassembler, a lookup table is used to translate each binary instruction into its corresponding assembly language mnemonic. The resulting assembly language code can then be viewed and manipulated by a human programmer.
Demonstration
Once a program is disassembled (in this case, the IDA disassembler is used), a reverse engineer can perform some operations such as searching for strings or manipulating program instructions. A curious engineer might begin by searching for the error message from Figure 1.3. In doing so, the engineer can find the program function that checks for matching registration codes and the instruction that outputs a message depending on the result. This program logic and associated assembly instruction can be seen in Figure 1.4.
FIGURE 1.4- Program Logic
By manipulating the assembly instructions using IDA’s patching functionality, an engineer can make the application jump to the “Correct Code” message each time an invalid username and registration code is entered. Figure 1.5 shows how this code is manipulated. Specifically, the “JNZ” or “Jump here if the values are not equal to Zero” is changed to “JZ” or “Jump here if the values ARE equal to Zero”.
Essentially, this portion of the program is comparing the valid generated registration code (byte_406B84) with the registration code that the user entered (String1). If these values are not equal to each other, the program will jump to the “Wrong Code” message prompt, otherwise it will jump to the “Correct Code” message prompt. By manipulating this logic, we can get the program to jump to the “Correct Code” message when the code is incorrect.
FIGURE 1.5 - Manipulating Assembly Instructions
The changes are then saved to the input binary executable file as seen in Figure 1.6
FIGURE 1.6 - Saving the Patched Binary
The executable can now be run to confirm that the updated logic works as expected. The incorrect registration code is entered, and the user is now shown the “Correct Code” prompt as seen in Figure 1.7.
FIGURE 1.7 - Incorrect Code Displays Correct Prompt
Taking it a step further, a reverse engineer may want to identify the legitimately generated registration code for any username - effectively creating a registration code generator (or keygen). Since the program’s logic is generating this code behind the scenes, a reverse engineer may be able to print the value into one of the message prompts.
Figure 1.8 shows how an engineer can replace the “Correct Code” prompt message with the value of the legitimately generated registration code (byte_406B84).
FIGURE 1.8 - Further Assembly Manipulation
After saving these changes and re-running the program, the user is then presented with a legitimate registration code for any username that is input into the program as seen in Figure 1.9.
FIGURE 1.9 - Revealing the Registration Code
Although this was a very basic demonstration, it highlights the logic manipulation that is possible in applications should they not implement effective security controls.
Current Threat Landscape
Due to the malleability of binary program functionality, threat actors can easily implant malicious program logic into software, which can be distributed online to unsuspecting users as a "Free Version" of a paid program. This approach has become a favored method for malicious actors to deliver malware onto users' devices since most users are not decompiling and analyzing their binaries before running them. Consequently, users are exposed to new avenues of malware infections.
It is worth noting that a simple online search of your favorite paid software, with the term "Cracked" prepended to it, will likely yield many suspicious results. While some of these sites may offer genuinely cracked software, users should be mindful of the risks associated with downloading and running any software from untrusted sources. Figure 2.0 shows some of the results that appear when searching for “Cracked Photoshop”.
FIGURE 2.0 - Cracked Software Distribution
These suspicious websites appear higher up in search results than one might expect and highlights a tactic that is being leveraged more and more by threat actors in the wild, which is the use of Search Engine Optimization (SEO) to add relevancy to malicious sites.
Threat actors can use various SEO tactics to improve the visibility of their websites that offer cracked software downloads. For example, they can use popular keywords related to the software, such as the name of the software, along with terms like "cracked" or "free download". They may also use backlinks from other websites to increase the authority and visibility of their site in search engine results.
To this end, threat actors have also been leveraging paid advertisements in order to further promote their malicious websites, relying on a search engine’s lack of validation or vetting process for their advertised sites, further proliferating malicious software downloads.
Although not a foolproof method, users should consider submitting unknown software to VirusTotal for analysis before running it on a local device. While VirusTotal will likely raise alarms for genuinely cracked software, the service can still provide insight into how security vendors are analyzing a known file. As always, if you want to stay 100% safe, the best form of protection is always abstinence.
Works Cited
Crackmes, https://crackmes.one/crackme/5ab77f5633c5d40ad448c2f0.
D. S. Wallach, "Copy protection technology is doomed," in Computer, vol. 34, no. 10, pp. 48-49, Oct. 2001, doi: 10.1109/2.955098.
Ida Free, https://hex-rays.com/ida-free/.
“Introduction to Compilers.” GeeksforGeeks, GeeksforGeeks, 4 Mar. 2023, https://www.geeksforgeeks.org/introduction-to-compilers/.
Markus Kammerstetter Vienna University of Technology, et al. “Vanity, Cracks and Malware: Proceedings of the 2012 ACM Conference on Computer and Communications Security.” ACM Conferences, 1 Oct. 2012, https://dl.acm.org/doi/10.1145/2382196.2382282.
Moyal, Maor. “Cracked Software Leads to Nitol Ddos and Amadey Bot Malware.” Cymulate, https://cymulate.com/threats/cracked-software-leads-to-nitol-ddos-and-amadey-bot-malware/.
“The Pirate Bay Trial: The Official Verdict - Guilty * Torrentfreak.” Go to TorrentFreak., https://torrentfreak.com/the-pirate-bay-trial-the-verdict-090417/.
Sigi Goode What Motivates Software Crackers? - People.anu.edu.au. https://people.anu.edu.au/sigi/goode_jbe.pdf.
Virustotal, https://www.virustotal.com/gui/home/upload.